
Contracting with an external professional to perform an onsite HIPAA audit might be a good option for you.
Learn to close data security gaps and prevent data breaches at your business.

What does this new enforcement plan actually mean for noncompliant merchants and service providers?

None of these seven suggestions requires changing or enhancing your clinical expertise.

Healthcare entities must be proactive about protecting sensitive data across their organization.
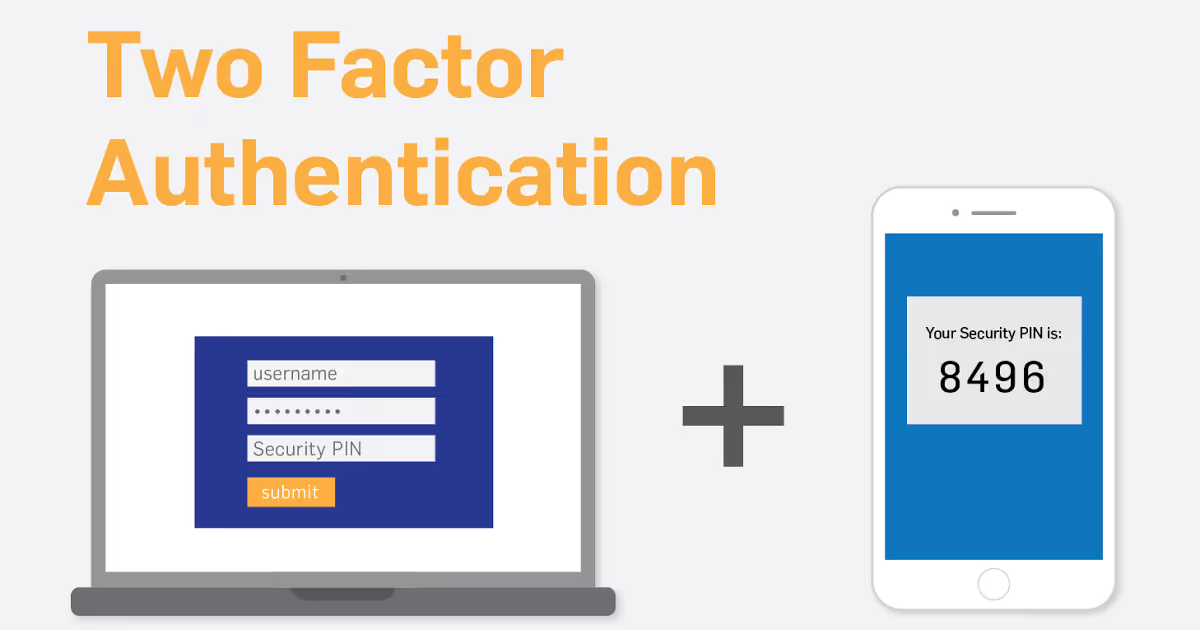
Is two-factor authentication perfect? No, but it does make a hacker’s job more difficult.

Each healthcare professional has a responsibility and stewardship over the patients’ PHI they handle.

The key to properly using PCI policies is communication.

Learn some tricks to getting your ecommerce business PCI compliant.

Learn more about the study the FTC is conducting on the PCI DSS assessment process.

Learn which areas of the PCI DSS business have the most trouble.

Learn more about the Dirty Cow vulnerability present in Linux systems and Android phones.

Here are some basic things your organization should know about HIPAA penetration testing.

Learn how your business is making itself a target with cybersecurity vulnerabilities.
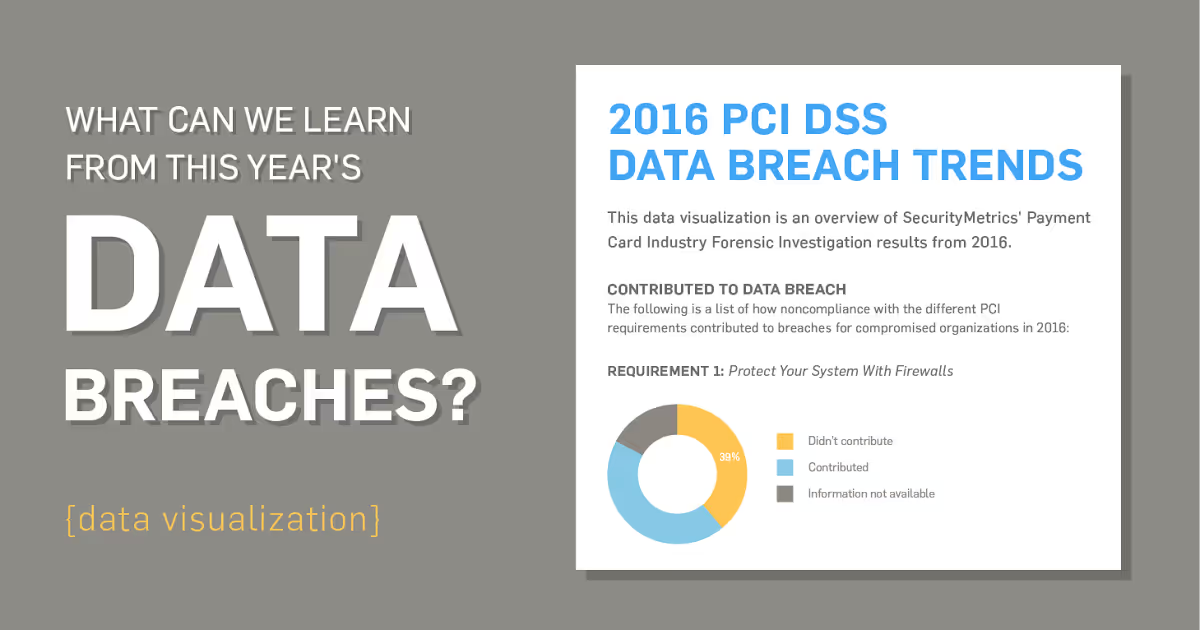
Things to remember from this year are password security, securing remote access, and PCI compliant firewalls.

See where many merchants still struggle with completing PCI requirements and SAQs.

Here are a few answered questions about the WannaCrypt attack and what your business should do to combat it.

What is phishing? Phishing refers to a type of social engineering that happens primarily through emails. Hackers will send emails that often have links to malware.

An in-depth look at the PCI Security Standard Council’s recent MFA guidance supplement and what it means for your organization.

Merchants use the 2018 SecurityMetrics PCI Guide both as a desk-side PCI reference and as a tool to direct and track their organizations’ internal PCI compliance efforts. But, there’s also another side to the Guide.
At SecurityMetrics, our mission remains to help you close data security and compliance gaps to avoid data breaches.
As plans to reopen economies move forward around the world, the entire cybersecurity industry–including the SecurityMetrics Security Operations Center (SOC)–is being challenged in new and unexpected ways.