A business continuity plan (BCP) provides a way for organizations to deal with the business impact of any disruptive event and carry on with business.

What is Vulnerability Scanning? Vulnerability scanners are computer programs that search systems for weaknesses.

Network security consists of the policies, procedures, programs, hardware, software, and people you use to protect your corporate network.
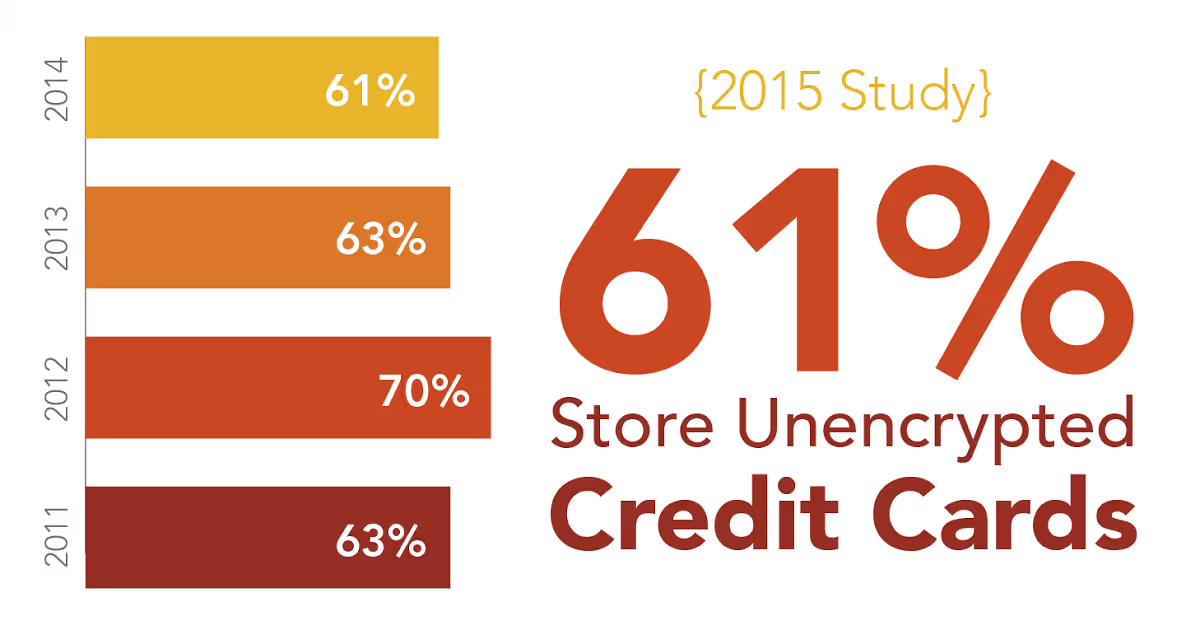
Payment card data can easily leak due to poor processes or misconfigured software.

These service guarantees exist to address the financial hardships your business might endure in the aftermath of a compromise.

This blog covers the important changes from PCI DSS version 2.0 and 3.0.

If businesses are determined to provide mobile solutions, it is their responsibility to educate themselves, ensure the security of the solution, and know the risk they’re taking upon themselves.

Shellshock, also known as the Bash Bug, is a software vulnerability that could make your systems vulnerable.

The plug-and-play mindset is ruining Point-of-Sale (POS) security.

If you have any questions, please contact SecurityMetrics support, 801.705.5700.

Find out how to use nature's defense mechanisms to protect your business.

Depending on how you outsource, you may be able to decrease your PCI scope and business risk.

If you have any questions, please contact SecurityMetrics support, 801.705.5700.

PCI version 3.1 was primarily released to address the insecurity of SSL and some TLS encryption protocols.

We define important PCI DSS acronyms and terms in this PCI audit glossary.

Portals made specifically for your patients offer data security that email never could.

The unprotected PHI problem is easy to fix, but it must start with you.

Once you have established that your records reflect reality, it is time to monitor to ensure they are accurate.
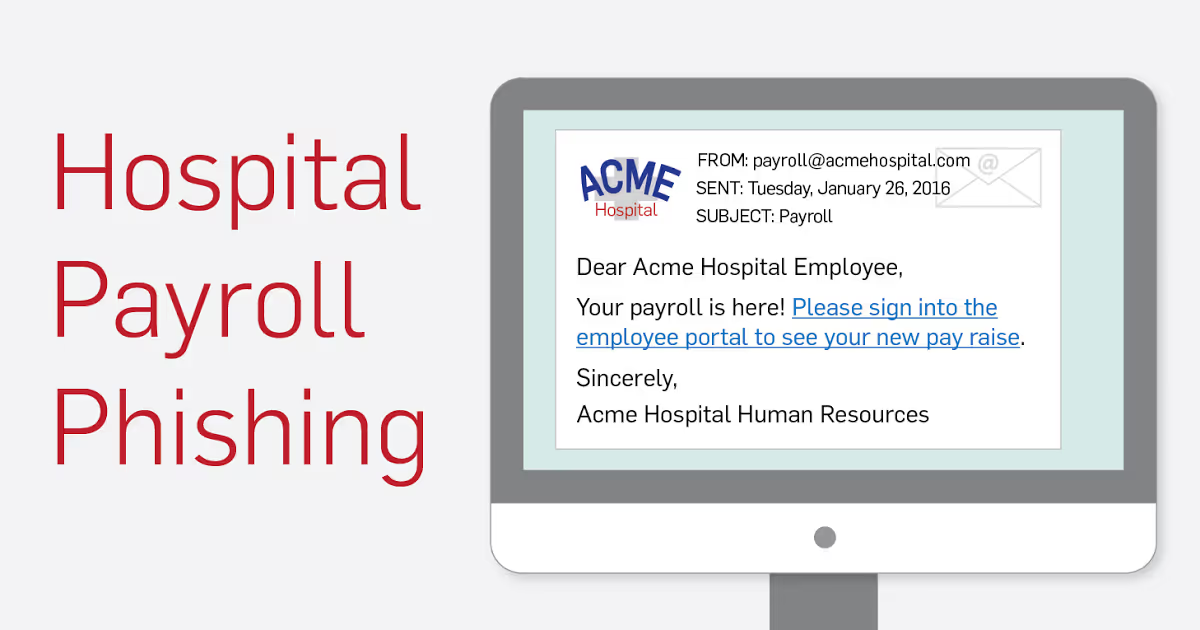
Essentially, the hackers steal paychecks from right under their noses.

My advice? Decide to take security seriously.

Vulnerability scanning is one of the only crucial things that can help companies keep up-to-date on emerging vulnerabilities.