
You can’t afford to be passive anymore; it’s time to be aggressive.
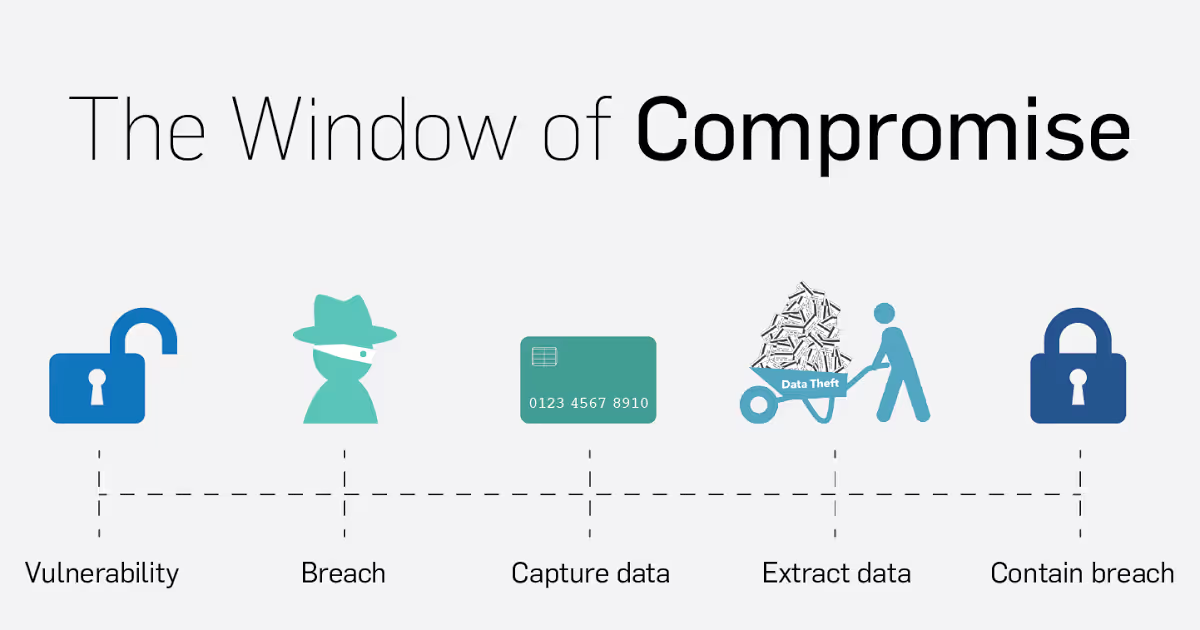
On average, a merchant was vulnerable for 470 days before an attacker was able to compromise the system.

See what changes PCI 3.2 brings and what you’ll need to do.

Learn what’s involved in the Phase 2 HIPAA Audit Program and how you can prepare.

Network security is more crucial than ever for healthcare providers.
HIPAA Compliance in “the cloud” Cloud data storage is a common and convenient option for healthcare organizations.

The best way to inspire better security practices is to show examples of true security blunders.

What happens when forensic investigators can’t find evidence of a compromise?

Hackers are getting smarter than our automated detection tools.

Hopefully, you'll realize some actions you should take to ensure your own business’ security.
Front desk clerks are friendly…sometimes to a fault, but friendly doesn’t necessarily equal secure.

The HHS says shredding, burning, pulping, and pulverizing are the only way these records should be destroyed.
Can customer service and front desk security co-exist?

Some falsely assume because mobile devices are technologically advanced and marketed as ‘secure’, PHI will automatically be protected.

To help further the fight against fraudsters and data thieves, the SecurityMetrics Forensic Investigation team has identified several common attack types associated with recent breaches.
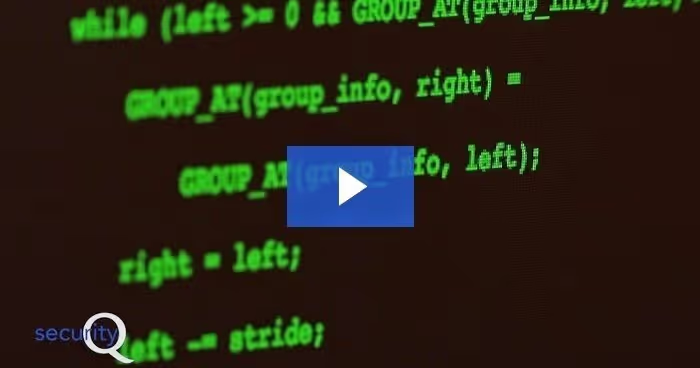
Cross-site scripting allows bad guys to embed malicious code into a legitimate website to ultimately steal user data.

When an exploit for WinShock is released, SecurityMetrics will work to include a check for the vulnerability in its vulnerability scanning engine.

Please educate yourself and your organization on the technology perils of our day.

If you have any questions, please contact SecurityMetrics support, 801.705.5700.

Don’t fall prey to these common HIPAA misunderstandings.
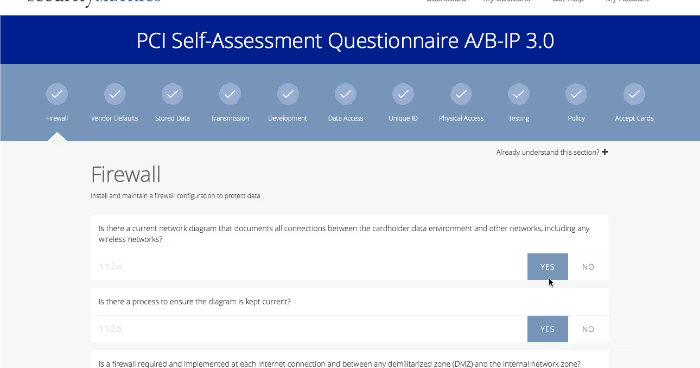
Learn about changes to our customer PCI validation portal to accommodate for PCI version 3.0
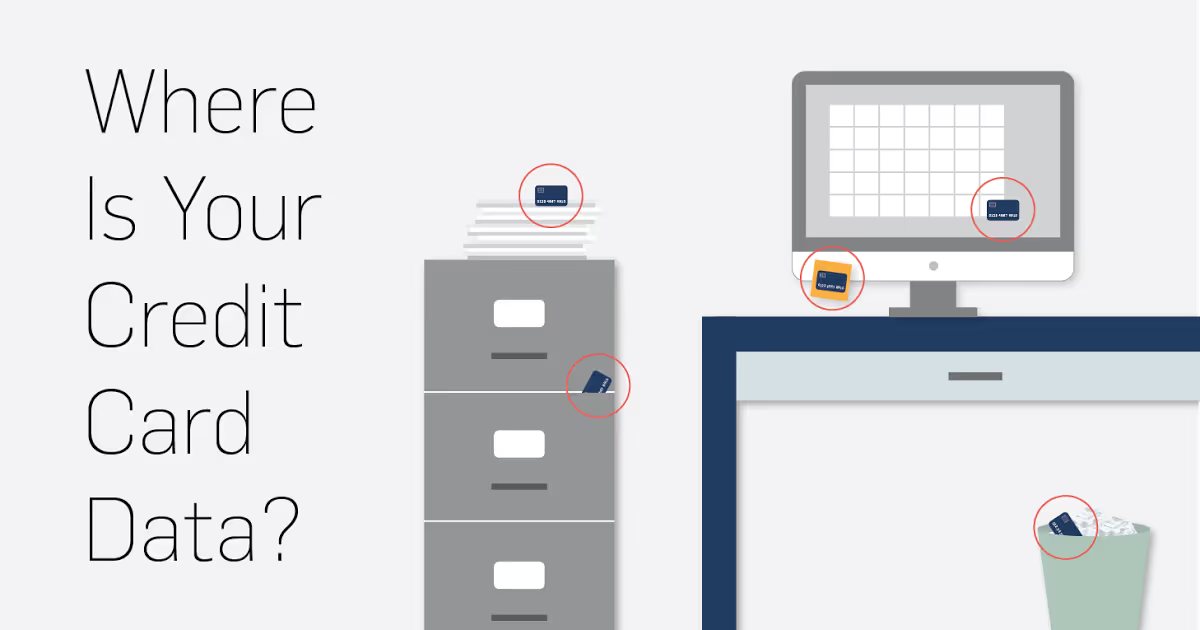
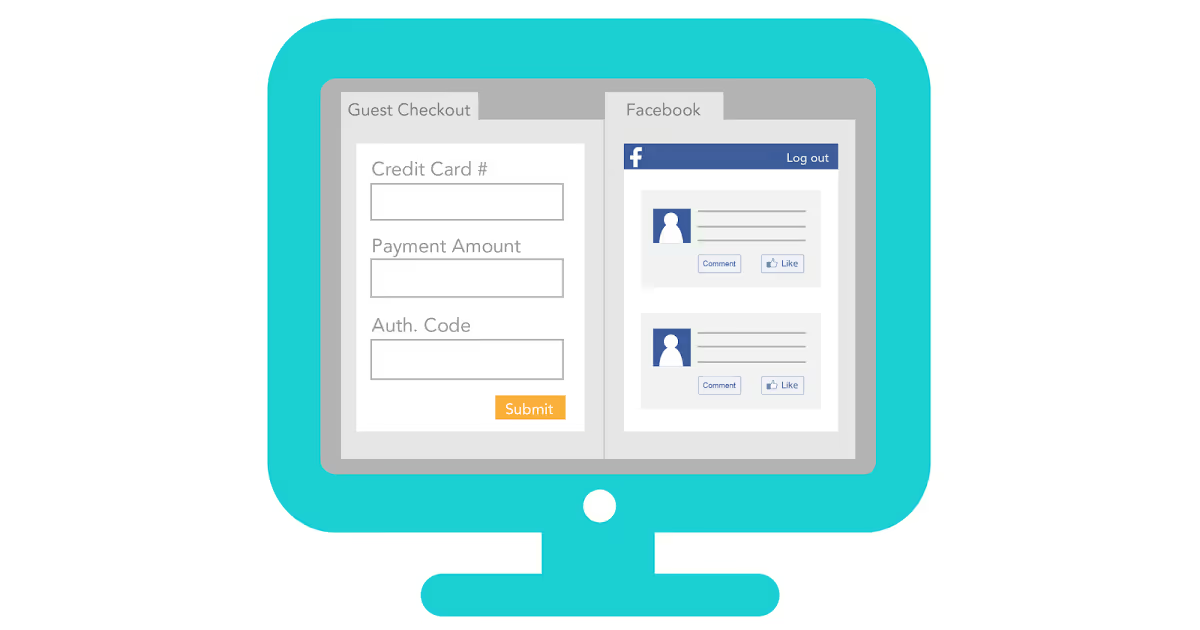
Unencrypted credit card data is hiding on your network